In this post I’ll explain what TOR network and Onion routing are. Separate article explains asymmetric encryption. To use this, of course, you need a TOR client / browser.
How to install TOR Browser in Linux.
Table Of Contents (T.O.C.):
- TOR network and Onion routing origins
- How does TOR network with Onion routing work?
- Uses of TOR network
- Final notes
1. TOR network and Onion routing origins
Tor is free, open source software for anonymous communication (in general). It is an acronym for The Onion Router. Onion is “(multi)layered encryption”, to put it that way (I’ll explain).
Onion routing was first developed in 1990s for US intelligence communication protection, at the US Naval Research Laboratory, by Paul Syverson, Michael G. Reed, and David Goldschlag. The development was helped by DARPA (who’s network, ARPANET, was the basis of the modern Internet). Onion routing was patented in 1998 by the US Navy.
Scientists Roger Dingledine and Nick Mathewson joined Paul Syverson in 2002 to start what would become known as the TOR project. When the Onion routing code was released under a free license, TOR was founded as a non-profit organization, in 2006.
Help BikeGremlin
stay online & independent
This website is educational, free, objective, and not commercial
(sponsors don’t enjoy paying if you mention all the product downsides that you notice 🙂 ).
If you find this site to be good and helpful,
and if $5 per month is what you can afford to set aside,
please consider supporting my work with a Patreon donation:
2. How does TOR network with Onion routing work?
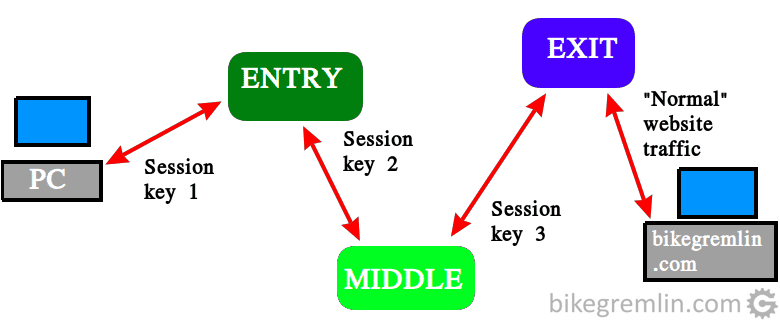
TOR network consists of a network of nodes, run on a voluntary basis. These are called Onion routers (or relays). For establishing the connection, a system of asymmetric encryption is used, with public and private keys. To explain better, I’ll use an example, say you wish to connect to bikegremlin.com using TOR network:
You will connect to your nearest TOR relay and exchange public keys with it. Then, TOR relay creates a “session password“, encrypts it using your public key (so it can only be decrypted using your private key, not know to others, so it is safe) and sends it to your computer. For further communication, the newly created, temporary session password is used.
Using the established encrypted channel, you can communicate with the nearest TOR router – called the “entry node” in the remainder of this text.
The same principle is then used to establish the communication between the entry and the second, “middle node“. A completely new session password is created, that is not related to the previously created one (the one used for the communication between your computer and the entry node).
While at it, the middle node has no idea whether the entry node is a computer connecting to the TOR network, or another TOR relay (entry node in this case).
This is then continued with additional nodes. There are usually between three and… many nodes used, though the total number is limited to preserve good performance. For simplicity, in this explanation, let’s say there are only three.
The last (in this case third) node is called the “exit node“. That las, exit node, then sends a request for showing the front page to the bikegremlin.com. As far as bikegremlin.com is concerned, exit node is the website visitor. It has no idea what is behind the exit node.
Likewise, if anyone is monitoring the communication between the middle and the entry node, all they will see are those two TOR routers exchanging some encrypted data. They will have no idea that the link is made and used to connect your computer to bikegremlin.com.
It might help taking a look at picture 1, then reading the explanation above again:
Picture 1
Advice: reading again the explanation above, then looking at the picture 1 could help to better understand picture 2. Picture 2 explains how a reply from the server gets encrypted with layers (like onion peels) of encryption, as it sets on its way to your PC.
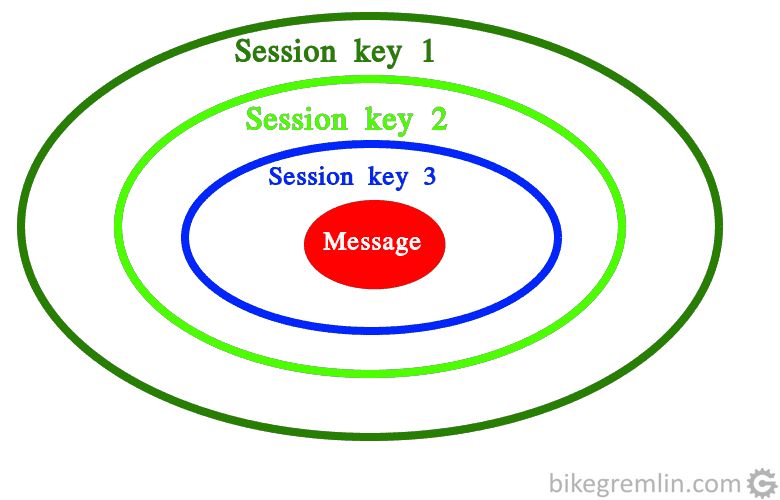
Picture 2
A message this “packed” goes from the server (bikegremlin.com in this example) to the exit node. Then gets sent to the middle, finishing at the entry node, before reaching your computer. Each node removes a layer of encryption, but there is no way for the website owner to know who wanted to see a page from their website – you are surfing anonymously.
I’ll repeat: all that anyone sniffing your computer communication can “see” is you communicating encrypted messages with the entry node. They won’t know what you are sending, what you are receiving, nor which websites you are visiting / who you are communicating with.
3. Uses of TOR network
OK, that’s all very nice, but what’s it good for?
Firstly, TOR enables anonymous surfing, communication in general.
Then, it allows “faking” your country of origin – you appear to be from the location where the TOR exit node is located at.
It is slower than a VPN, but your anonymity doesn’t depend on whether the VPN providing company keeps your data, or not. Though torrent download will last ages – don’t use TOR for that, you’ll just be choking the network for all the other TOR users.
On the other hand, if you live in a country that doesn’t respect privacy and/or freedom of speech (which one does?), then TOR is a good solution for communicating anonymously.
4. Final notes
I believe this is understood for most people, but I’ll mention it just in case:
If you log into the website using your user name, or buy something using your credit card, of course it would be able to track you – you have “introduced” yourself. Oh, and logging into your Facebook, Gmail etc is probably not a good idea if you wish to remain anonymous, it will be like saying: “Yes, I absolutely wish to remain anonymous, first to say that my name is…”
Also make sure that your computer and browser are safe, not compromised (no viruses, malware etc.). TOR is not all-powerful (in spite of the name), so all the standard “fishing tricks” are still on – don’t be careless and naive.
Finally, my personal impression is that USA has the means to break this encryption, otherwise they wouldn’t have let it be free and publicly available. But most other “big brothers” will most probably be stopped by TOR. Colour me paranoid.

