In the post about securing (WordPress) websites, I wrote about the importance of SSL/TLS encryption (and using https protocol). What the protocol is based on is asymmetric encryption. In this post I’ll explain briefly, in “plain English” what asymmetric encryption is. It is important to understand this encryption mechanism, so that other security and privacy based topics can be understood and so that good advice on those topics can be discerned from bad advice. Internet is full of both. A separate post explains the term of “multifactor (two factor) authentication“.
Table Of Contents (T.O.C.):
- Asymmetric encryption definition
- Problems – Tasks
- Digital fingerprint – “Hash”, or “Message digest”
- Encryption
- Asymmetric encryption
- Sending and receiving a message
- PKI – Public key infrastructure
- Asymmetric encryption explanation using a practical example
1. Asymmetric encryption definition
Asymmetric encryption can be explained in one sentence. Just memorize the following sentence and then you’ll be able to, using simple logic, figure out how to solve the presented problems, using the “tools” given in the following sentence:
We have a pair of two keys, such that anything encrypted (“locked”) using one can be decrypted (“unlocked”) only using the other key.
2. Problems – Tasks
Modern communications present us with the following problems (among others) when exchanging data/information, that can be solved using various tools:
- Secrecy – only the recipient may see the (decrypted) data.
- Authenticity – the recipient has a confirmation that the one sending the data is who they claim to be.
- Integrity – the recipient has a confirmation that the data has arrived unchanged (as it was sent).
- Undeniability – the sender can’t deny having sent the data (can’t claim someone else sent it).
All the above listed problems can be solved using asymmetric encryption (though the first one can be solved using symmetric encryption as well) and hash function. By the end of this post, you’ll understand how exactly.
3. Digital fingerprint – “Hash”, or “Message digest”
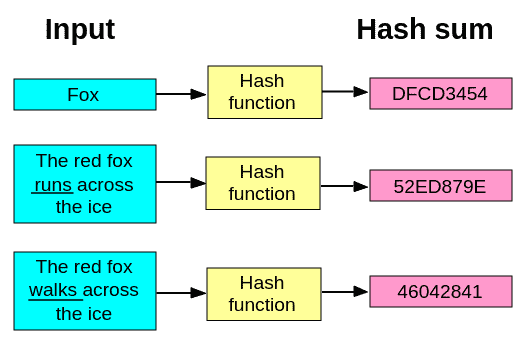
In order to fully understand asymmetric encryption, it is important to understand another term: “hash”. Hash is a mathematical function that creates a digital fingerprint of the data that is of a predetermined length (depending on the function used, this can be 128 bits, or 256 bits, or more/less). An example of hash function use:
Picture 1
All the below listed characteristics of a hash function, except the last one, can be deduced from the picture 1:
- Applying hash function to the original data gives a digital fingerprint (hash) of the same length.
- Even minor data change results in a drastic change of its hash value.
- Original data can’t be reconstructed from its hash sum (hash value).
Characteristics listed above are of crucial importance. For example, hash of a sentence “English breakfast.” and a hash of the complete “Lord of The Rings” trilogy will be of exactly the same length (in the range of 256 bits, depending on the used hash algorithm). Also, hash values of words “gremlin” and “gremlins” will be drastically different. Finally, from the given (calculated) hash values, it will be impossible to conclude the contents of the original data – hash is a “one way function” (correct term is “irreversible function”).
Hash is also called a “digital signature” – that’s what it is.
4. Encryption
Unlike hash function, encryption (however it is achieved) has the following characteristics:
- The size of the encrypted data depends on the size of the original source data that was encrypted (technically this doesn’t have to be the case, but in practice it is).
- Original source data can be reconstructed (using an appropriate decryption key).
Now I beg you to read the first three chapters again. Repeat and memorize the last (in bold) sentence from chapter 1. Then understand and memorize the difference between hash function and encryption. Finally, try to figure out how you would solve the problems listed in chapter 2 using those tools.
This was not a test whether you are a robot (and would end up in an infinite loop) – it really is important that the first three chapters have “sunk in”. 🙂 Now we can continue.
Encryption can be:
- Symmetric – one (same) key is used for encryption and decryption.
- Asymmetric – uses a pair of keys. I.e. two generated keys make a sort of a special union, such that anything encrypted by one key can only be decrypted by the other key (from the same pair) – and vice-versa.
Symmetric encryption is faster (less resource demanding) than asymmetric encryption. The main problem with symmetric encryption is how can I exchange the one secret key with the correspondent, so that it can not be seen / intercepted / stolen by anyone else.
This practically requires for us to meet and exchange the key. Additional problem is if we don’t know each other personally, or if we are far away from each other. The bottom line is – exchanging a symmetric encryption key can be rather inconvenient. Unless we use asymmetric encryption!
Asymmetric encryption allows us to exchange a secret key (used for symmetric encryption) over the Internet, in a secure way, so that no one can steal / intercept it! How that is achieved is explained below.
5. Asymmetric encryption
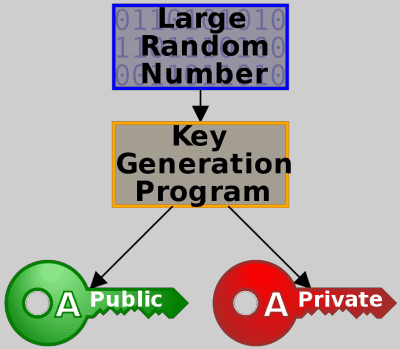
As mentioned above, asymmetric encryption is based on a pair of keys:
- One key is known by everyone, that is the public key.
- Other key is known only by the pair owner, that is the private key (secret key).
Picture 2
So, everyone knows (has) my public key, but only I know (have) my private one.
Same goes for Jane’s, John’s and Batman’s key pairs: we all know everyone’s public key, while the private is known only to the person who owns the key pair.
Now let’s repeat: anything that is encrypted using one key can only be decrypted using the other key (from the same pair of keys).
6. Sending and receiving a message
Remember the problem from chapter 2 – it is needed to achieve:
- Secrecy – only the authorised may see the (decrypted) data.
- Authenticity – the recipient has a confirmation that the one sending the data is who they claim to be.
- Integrity – the recipient has a confirmation that the data has arrived unchanged (as it was sent).
- Undeniability – the sender can’t deny having sent the data (can’t claim someone else sent it).
A sender of a message (data) can achieve this using asymmetric encryption (and hash function). In order to do it, the sender has to:
- Creates a hash of the original message (data).
- Encrypts the created hash with his/hers private key.
- Encrypts the original message with the recipient’s public key.
- Sends data created under 2. and 3. to the recipient.
Recipient then has to:
- Decrypt the message using his/hers private key.
- Decrypt the received hash using the sender’s public key.
- Create a hash of the decrypted message (got under 1.).
- Compare hash they got under 2. with the one created under 3.
Results of this procedure
Sender is certain that:
- the message can only be read (decrypted) by the intended recipient.
Recipient is certain that:
- the message could only be read (decrypted) by him/her.
- the message was sent by the person claiming to have sent it.
- the sender can’t deny having sent the message.
- the message was not altered on the way (in transit).
If you don’t understand why the sender and the recipient are so certain of the above listed claims, read again what encryption and hash function are, then remember the rule of asymmetric encryption:
Anything that is encrypted using one key can only be decrypted using the other key (from the same pair of keys).
7. PKI – Public key infrastructure
In practice, asymmetric encryption is implemented by relying on Certificate Authoritiy (CA). Certificate Authority is an organization (or an institution) that issues digital certificates, i.e. pairs of private and public keys. In order for such a system to function, Certificate authority must be trustworthy. That is: everyone must trust the CA.
So, CA does the following:
- Checks (confirms) the owner’s identity.
- Creates a pair of keys (public and private).
- Connects the owner’s name with their public (and private) key. This is called “issuing a digital certificate“.
- Signs the issued certificate with CA’s private key.
- Announces this publicly (CA also announces digital certificate expiry date, lists invalid certificates etc.).
Digital certificate = owner’s name and info + owner’s public key, signed with CA’s private key.
The bottom line is: everyone must trust the CA. Asymmetric encryption can not exist (function) without a trusted CA.
8. Asymmetric encryption explanation using a practical example
Since for me it was easier to understand this way, I’ll use an example for explanation. First let’s repeat the key sentences (pun intended 🙂 ):
Asymmetric encryption:
- Anything that is encrypted using one key can only be decrypted using the other key (from the same pair of keys).
Hash:
- Applying hash function to the original data gives a digital fingerprint (hash) of the same length.
- Even minor data change results in a drastic change of its hash value.
- Original data can’t be reconstructed from its hash sum (hash value).
Let’s start now with an example. Say that I want to send a message to Batman (regardless whether it is a letter, or some files – we’ll call it a “message”). So that only Batman can read it. And so that Batman, upon receiving it can be certain that it’s been written by the colleague superhero Bike Gremlin, not by some swindler impersonating me.

- Since I have no idea who the man is (no spoilers here, no sir!), I’ll have to ask the Certificate Authority (CA): “what’s Batman’s public key?”
- How can Batman be certain that the message was sent by Bike Gremlin? I’ll digitally sign it. I do this by making a hash of the message. Then I encrypt the hash using my private key.
- Now I can encrypt the message using Batman’s public key, so only Batman can decrypt it (using his private key).
- Together with the message, I’ll send the hash I had encrypted with my private key.
A few seconds later, in Gotham:
Batman sees he has a new message. From “Bike Gremlin” – “Bat-cycle prototype blueprints”.
Figuring: “this could be cool, unless Joker planted a trick to get me killed while riding. Let’s check.”
- Batman decrypts the message using his private key. Now he wants to confirm that the message was in fact sent by Bike Gremlin.
- In order to do that, he first makes a hash of the message.
- Then he asks the CA: “What is Bike Gremlin’s public key?” and uses that key to decrypt the hash I had sent.
- Finally, he compares the decrypted hash with the hash he made. If they are the same, he can be certain the message was sent by Bike Gremlin and no one else. At the same time, if brakes don’t work properly, I won’t be able to blame Joker for planting the blueprints, since my digital signature confirms that I was the author.
What is commonly used in practice is to use this mechanism to exchange keys for symmetric encryption. So, I can use asymmetric encryption to send a message that says:
“Hi Batman, this is Bike Gremlin. In order to communicate faster and not bother the CA all the time, let’s use symmetric encryption from now on. We could use ‘Marvel sucks’ as encryption password. “
I’m begging the readers not to tell this password to anyone, or we’ll have to come up with a new one.
– Yours truly, Bike Gremlin
When you come to a website, using https protocol (TLS encryption) something similar to this happens. Asymmetric encryption is used to confirm identities and securely exchange keys for symmetric encryption, which is used from then on. This is called: “HTTPS handshake“.

