In this post I’ll explain what SSL/TLS certificates are, what kinds exist and what are the differences.
1. What is SSL/TLS?
SSL (Secure Sockets Layer) is a protocol that enables encrypted communication between computers. For an explanation how it works, private and public keys, certificate authority and HTTPS handshake, read the article on asymmetric encryption.
After version 3.0, SSL was renamed to TLS (Transport Layer Security), instead of naming it SSL 4.0. Newest TLS version is 1.3. While everything below TLS 1.2 is considered insecure. In practice, it is still usually referred to (wrongly) as SSL.
Separate posts explain how to install SSL/TLS in cPanel and how to install them in DirectAdmin.
2. Types of SSL/TLS certificates
There are three types of these certificates:
- DV (Domain Validation)
- OV (Organization Validation)
- EV (Extended Validation)
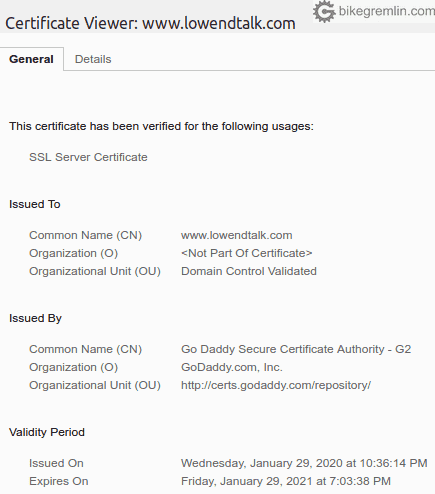
2.1. DV (Domain Validation) certificates
They are automatically issued. If you have control over the DNS, you’ve can get it and install its private key on your hosting server. Certificate is issued to the domain.
Picture 1
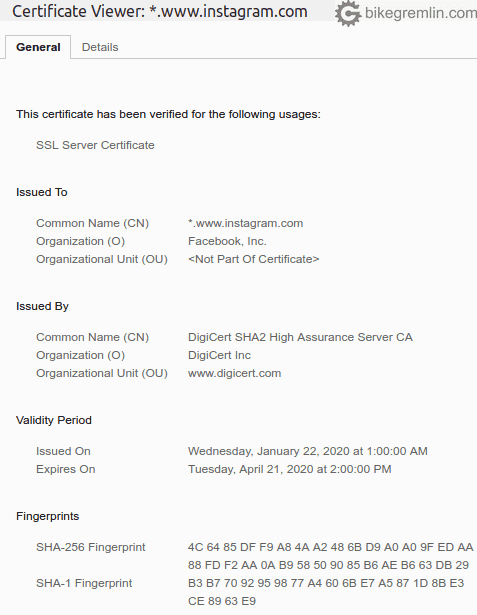
2.2. OV (Organization Validation) certificates
Here a basic background check is done. Certificate is issued for the owner (organization) and some proof of company registration is required. Of course, it is “tied” to the domain it is issued for.
Picture 2
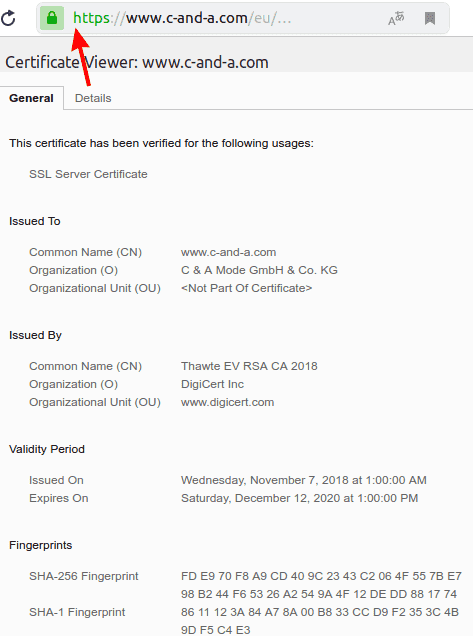
2.3. EV (Extended Validation) certificates
Similar to OV, but with a bit more thorough identity check (done by humans, not automated). To confirm that you are indeed who you present yourself to be – i.e. that your company is really registered and it exists.
Picture 3
3. Free and paid SSL/TLS certificates
Free SSL/TLS certificates are issued only as DV. The most popular free ones are issued by Let’s Encrypt. For the paid DV certificates, prices go from about 10$ per year.
OV certificates are more expensive – prices go from about 50$ per year. All OV certificates are paid for.
EV certificates are even more expensive, with prices starting from about 100$ per year. EV certificates are all paid for.
3.1. Wildcard certificates
What is a wildcard certificate? It is a certificate issued for one domain (or one subdomain), so that it is valid for its 1st level subdomains. Does this sound a bit confusing? In addition to my explanation of domains and subdomains, I’ll make an example:
My website uses a free wildcard DV certificate that is issued for *.bikegremlin.com. Which means it covers io.bikegremlin.com, bike.bikegremlin.com, www.bikegremlin.com, bikegremlin.com…
But it doesn’t cover www.io.bikegremlin.com, nor www.bike.bikegremlin.com. For that would require two additional certificates.
Now, I could get a wildcard certificate for *.io.bikegremlin.com, which would cover say linux.io.bikegremlin.com, wordpress.io.bikegremlin.com etc. But it would not cover shop.bike.bikegremlin.com. For that would require yet another certificate, either for that particular (2nd level) subdomain, or a wildcard certificate issued for *.bike.bikegremlin.com.
Note that free certificates can be issued only for 1st level sudomains, so the examples in the paragraph above would require paid certificates (either DV, or OV). Also, as far as I know, there are no wildcard EV certificates. There are EV certificates that cover multiple (sub)domains, but each has to be noted when the certificate is issued.
Paid wildcard certificates are about 10 times more expensive, compared to those issued for one (sub)domain – this goes for both DV and OV certificates. Same high price goes for multi-(sub)domain EV certificates.
3.2. Certificate validity period
All the SSL/TLS certificates have a set validity period. After that period has passed, they have to be renewed (re-issued).
Validity period for free certificates is 90 days. Renewal can be configured to be automatic. Usually best set to renew after 60 days, so that in case of any auto-renewal problems, there is plenty of time to get it fixed.
Free tool HetrixTools (affiliate link) enables automated monitoring and notification when an SSL/TLS certificate has only 15, or 30 days left before renewal. I find that useful.
Paid certificates can have a validity period of up to 825 days (27 months, just over 2 years). They are usually issued with one, or two year validity period.
3.3. SSL/TLS certificate security
It may be counter-intuitive, but shorter certificate validity period leaves less time for hackers to crack it, before it is obsolete and a new one is issued. In this respect, the free Let’s Encrypt certificates, with their 90 day validity period, can be considered safer than paid certificates issued with a year, or two year validity period!
The shorter validity period for Let’s Encrypt was enforced because people were (are?) less trustworthy towards this free solution. Many people still believe that if they pay for a certificate, that certificate authority is more secure, more “serious”.
As I’ve explained in the post about asymmetric encryption, the system of public and private keys (on which SSL/TLS is based) depends on security and trust of certificate authority (CA).
Also, it is important to know that SSL/TLS encryption is not be all end all when it comes to security. Websites can be hacked in spite of it. Of course, it will definitely make the hackers’ job more difficult, especially if they are trying to read the data that you, or the website visitors, are sending to, or getting from the website (such as login passwords, private data etc.).
EV certificates, because of stricter background checking when they are issued, will tell those visitors who know how to analyze a certificate that it is very likely that you are who you say you are.
For example, I make a shop.bikegremlin.com. Then someone registers shop.bikegremlin.us and coppies my design. Then I register BikeGremlin Co. and get an EV certificate to that name. It would be next to impossible for an impostor to get a certificate to the company with the same name. Which might help if visitors bother to check the certificate, but very, very few do.
Most paid certificate issuers offer some sort of insurance, in case of any damages done due to a certificate being cracked/hacked. If you can prove you’ve suffered some losses due to certificate problems, you might be able to get some money. However, all the other problems (data loss, or stolen, domain and IP reputation loss etc.) will be down to you to sort out.
4. Cloudflare and SSL/TLS
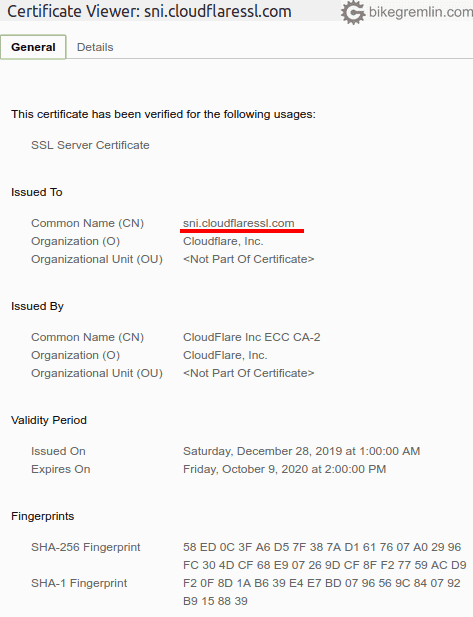
Finally, one catch related to Cloudflare. Cloudflare can be configured so that visitors connect to their servers via an encrypted protocol, but so that Cloudflare’s connection to your server is done via unencrypted connection. There is no way for visitors to know whether that is the case.
If Cloudflare free package is used, visitors will see something like this (regardless of how the connection to your server has been made):
Picture 4
If paid Cloudflare package is used (with, or without a paid certificate), visitors will see your domain (or company, depending on the certificate type) info, but there are still no guarantees on whether the connection from Cloudflare to the hosting server is encrypted.
In a separate post I explained what Cloudflare is and how it is configured for a website.
In the post about Cloudflare DNS setup, I explained what happens to user data on Cloudflare servers, even if encryption is used.
5. My personal opinion
Some large companies, like Amazon, don’t use EV certificates. Very few people bother to check and analyze certificates when they are on the website. While impostors can be dealt with legally.
For smaller, still less known web-shops, it might make sense to get more visitor trust by having a green padlock and browser bar, for those few visitors who do bother to look for that. Making them feel more secure by having a (paid) EV certificate.
Also, it can happen that competition, or an independent geek, publishes publicly that this-and-this shop doesn’t have an OV, or EV certificate. “How unprofessional!” “How can the visitors be safe?!”
Really, it all boils down to how people feel, and what/who they believe. An average Jane/Joe might read this whole post and still be clueless. Does at least one in 10,000 people check certificates of websites they visit? Or are the vast majority happy as long as they see the padlock icon in the browser?
Picture 5
Technically, Let’s Encrypt free SSL/TLS certificate is no less secure than any expensive EV one.
Google forces SSL/TLS encryption, by providing a ranking bonus to websites who use it (hence practically penalizing those who don’t), even if those are static .html sites, not gathering any user data.
Also, even though the modern, faster, HTTP/2 protocol doesn’t require SSL/TLS encryption, modern browsers (Google Chrome, Mozilla Firefox etc.) won’t load a site using HTTP/2 unless the website is run with the encryption (over https protocol).
So, SSL/TLS practically has to be used, whether it is really needed, or not. Still, there is no technical reason to pay for the certificates and not use the free Let’s Encrypt. It all boils down to how much trust do visitors have for the website/webshop they are visiting. Regardless of what type of certificate is used.
Update 2022: most mondern browsers no longer show a “green padlock” for websites with an EV certificate, so the EV certificate no longer has a practical advantage of increasing the level of trust that average website visitors have. In addition of technically not being any “more secure.”
Last updated:
Originally published:

