The service from the title is explained in a separate post: Cloudflare explained (what it offers, how it works). Another post offers detailed explanation of DNS and DNS records. In this post I’ll explain Cloudflare DNS setup in detail.
Note:
See my forum’s discussion thread about “Cloudflare being shady” – and consider that before deciding whether to go with Cloudflare.
1. Introduction – starting DNS setup
If you already have DNS set for your website, and then move the site to Cloudflare (by changing nameservers to Cloudflare’s), Cloudflare will automatically import all the DNS settings (so you won’t have to start from scratch).
I’m writing this tutorial in case you have to start from scratch, reasoning that it’s easy to skip parts that needn’t be done (that you see are already properly set).
2. Cloudflare DNS settings
With Cloudflare, DNS records are added and edited in DNS menu:
Choose “+Add record” (2) to add new
or click on any record’s value (3) to edit an existing one
When done, click on any other menu option (like “SSL/TLS”) and changes will be propagated
Picture 1
For example we’ll take an existing website, then explain all that was set – how and why:
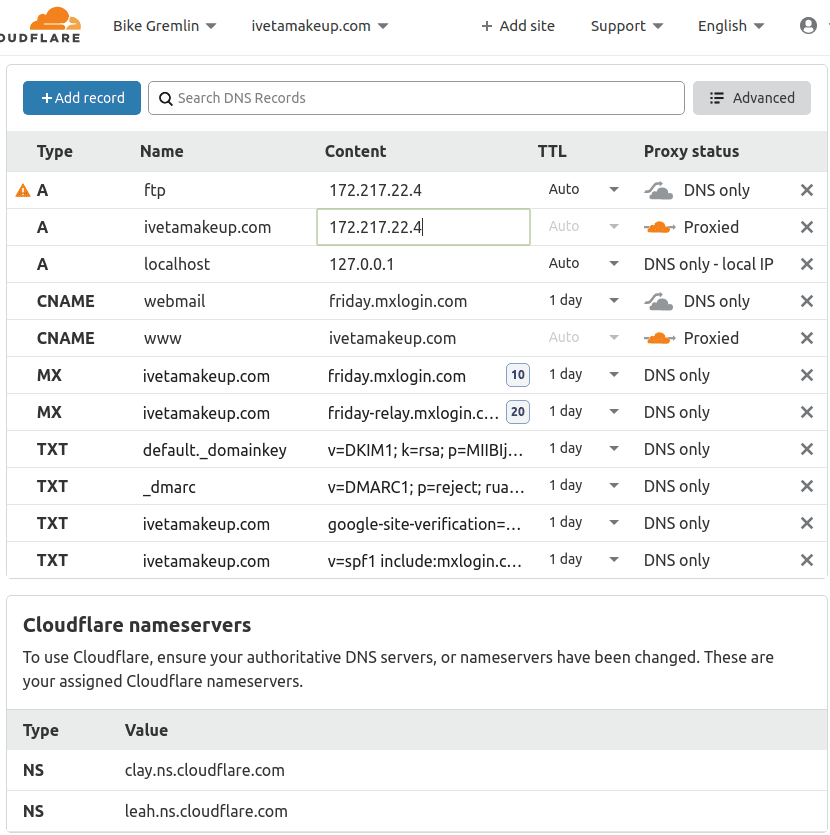
Picture 2
For explanation of MX and TXT records – and all the others – read my (above already mentioned) post on DNS setup. Same goes for explanation of TTL value.
Now look at the picture 2 and note grey clouds (“DNS only”) and orange clouds (“Proxied”). What is the difference? Orange cloud settings use Cloudflare as a proxy. “Fine, but what does that mean?” you may think now. Let’s explain.
Look at the first A record, that says:
A ftp 172.217.22.4 DNS onlyThis record sends anyone looking for ftp.ivetamakeup.com to the IPv4 address 172.217.22.4. Directly. Making that address publicly visible to anyone who queries DNS records for ivetamakeup.com domain.
Now look at the second A record in picture 2, with an orange cloud:
A ivetamakeup.com 172.217.22.4 ProxiedThis record is for the (naked) domain ivetamakeup.com. However, it will not reveal the IPv4 address, but all the visitors will be sent to a Cloudflare server that is nearest to them. This way Cloudflare acts as a proxy. It analyses requests, providing a basic protection from potential attacks. It can also serve pages and images from its cache (working as a sort of a CDN), thus relieving the hosting server and providing greater page load speed to website visitors. In a separate post I provided an explanation of caching, proxy and CDN.
3. When should you not use Cloudflare proxy?
Services such as mail and FTP don’t work when there’s a proxy like Cloudflare in between. Same goes for cpanel.mydomain.com. These will only work with a “gray cloud”, when Cloudflare acts as an ordinary DNS.
How to make website protected (without revealing hosting server IP address), while still having functional mail and FTP? Here’s how I do it (not claiming there aren’t other, perhaps even better ways, let me know in the comment section if you figure it out):
You could use hosting provider’s links for FTP. Logging in through your hosting account to reach control panel. Also, you could set up a “working” domain.
For email, it is best to use a separate service (not the one provided by many shared/reseller hosting providers), such as MXroute for example.
If we set it up this way, first record in picture 2 can be deleted. This way no DNS record would lead directly to the hosting server.
Another problem can happen when installing SSL/TLS certificates for the first time. I’ll write a separate post on that topic when I find the time. For now, the link in the first sentence of this paragraph will have to do, along with this link, explaining SSL/TLS certificate installation in DirectAdmin control panel.
Until I write the post, I’ll explain the most important, briefly:
If you are using Cloudflare and haven’t already installed SSL/TLS certificates on the hosting server, they may not install correctly for any DNS records that are proxied through Cloudflare (orange cloud). Also, you won’t be able to install, nor renew certificates for DNS records that aren’t defined in Cloudflare, since that is now your nameserver/DNS.
So pay attention when choosing which records to install the certificates for (check only those that are needed and defined in Cloudflare). Such “restrictive policy” is also good for protection, because it narrows the attack surface area. No one can abuse ftp.yourdomain.com if it doesn’t exist. I think this is a good use case for “security through obscurity“.
4. Conclusion and final notes
Cloudflare, in its free package of services, offers more benefits than it complicates things.
It enables faster website migrations, because in case of any errors, visitors can be pointed back to the old server until it is all sorted out, by just changing A record IP addresses. DNS propagation with Cloudflare is very fast, often taking under two minutes for records that are proxied through Cloudflare.
In addition to protection, it shortens page load times for website visitors that are far away from the hosting server – though for those near the server, it adds a few tenths of a second. On average, page load times are shorter, at least in my experience.
4.1. Author’s personal opinion
Take the information in this chapter as my personal opinion, ie: “to the best of my knowledge”, or “as far as I know”.
Important: related to any data encrypted using SSL/TLS encryption (https protocol) on the way to and from your hosting server. All that data gets decrypted on Cloudflare proxy servers (unless you use “gray could”, when Cloudflare acts as an ordinary DNS). They are then re-encrypted on the way to and from the website visitors. Otherwise caching and protection wouldn’t work. This means that Cloudflare (owners) can read all the data. They can record it, sell it, show it to anyone. They can even alter it if they wish, working as a man-in-the-middle attacker.
Does Cloudflare do this? They swear they don’t. It would certainly harm their reputation. Also, their business model is based on up-sales of extra services, so I don’t think they need to sell customer data (unlike some other large corporations). Still, I think it’s only fair for me to let you know that, technically, they could do that. Like Google, Cloudflare is a big brother that (for now) smiles gently and offers us a lot of great stuff for free. I’m using it, though my websites are set up so that they could easily work without it.
If you read this phishing attack attempt incident report at Cloudflare (Cloudflare website link), you’ll understand why I believe Cloudflare’s security is way above average.
Last updated:
Originally published: