Many times I’ve heard the following stories: “I hired a freelancer for website design, then there was an argument/misunderstanding, now I’m being blackmailed for losing the website and/or domain if I don’t pay”. Or: “I’ve registered the domain through a hosting provider, now I want to change the provider, what happens with the domain?”. In this post, I’ll address those and similar issues, explain how to prevent any problems and – as the title says – secure both your domain and the hard work put into the content creation.
I’ll briefly explain the bigger picture, related to security, because I think it is needed in order to understand, instead of just doing as told. Make a coffee, or a tea, this is going to be long, but it might just be worth your time – though I must say that the 30 minutes spent on reading this post will never be refunded.
Table Of Contents (T.O.C.):
- Introduction
- Website attack vectors explained
2.1. Social engineering - Weakest link – security as a chain
- Layers – security as an onion
- Domain and website security – the big picture
- How to protect yourself if hiring a developer / freelancer
- My personal opinion and experience
- Video – How to make strong passwords and store them securely
1. Introduction
First a disclaimer: I’m not a security expert. All the info given here (as all the other articles on the website) is based on my knowledge and experience so far, to be taken as: “to the best of my knowledge”, or “as far as I know”.
There is a good saying: “you can’t cheat an honest man”. In other words, most frauds are based on human greed: people don’t want to miss what looks like a great opportunity, so they don’t pay attention, nor use common sense (like: “what’s in it for you?”, or “how do you make a profit out of such an arrangement?”).
Likewise, many people believe things they read, or see – without reasonable scrutiny.
An example of this last point are WordPress plugins for redirection, used when the permalink structure is altered. In older versions, WordPress didn’t make automatic redirects. Now it does – it will automatically do 301 redirects from the previous permalink structure to the new one. I wrote an article on WordPress permalink structure change and redirects. Yet, there are loads of articles on the Internet where people say you need a plugin, or .htaccess redirects when you make a change in your permalink structure. This is not true (the testing method I’ve used to confirm this is provided in the above-linked article).
On that account: re-read the bolded sentence in the paragraph above (the second sentence). You know what? I have no idea whether it is correct (the part about the older versions of WordPress not doing automatic redirects – I’ve never tested that). Did you take my word for it? See what I’m talking about? I usually don’t do this – it was just in order to demonstrate a point. I try to make it clear when I only presume something, without having tested and confirmed it. Does everyone do this? Do most people do it? In my experience, many people repeat what they’ve read / heard, without having tested it, stating it as a fact. Like parrots, I’d say.
Critical thinking, reasoning and common sense, along with some caution get you a long way in terms of security.
To finish this long introduction with a few words on developers/freelancers: many of them rely on good reputation and recommendations. I believe that most are not trying to trick anyone. Many problems I got to experience or hear about were usually due to misunderstanding, poor communication, not defining what needs to be done clearly enough, or clients not understanding the process of building a website (in spite of being explained). For example:
“It’s a great website, could you just add a second language? You know – just add those small flags for choosing a language?”
Can’t think of a better example right now, but for this one: not every WordPress plugin supports multi-language and some that do, require a paid plugin version for that functionality – which all adds costs and/or asks for more time (which also costs – freelancers that work for free, usually starve). A function that might seem trivial to a client, so they forget to mention it at the start, might end up complicating things and adding costs (in both time, and money).
2. Website attack vectors explained
Attack vectors are an important term/aspect that should be understood. In order to explain better, I recommend we imagine website (or domain, or whatever is being protected) as a house and consider the attack vectors:

Picture 1
Vectors of attack are represented with red arrows. For anyone wanting to get into the house, without being authorized, attack vectors 1 and 2 would probably not make a lot less sense and would cause a lot more problems, than using attack vector 3 – through the glass door.
In those terms, when considering security, it is important to first secure any weak points, as well as most likely (most often used) vectors of attack (weak points and commonly used vectors of attack are not always the same). For picture 1: placing bars on the doors and windows, with good locks, would probably be a good starting point.
To make things worse, vectors of attack are not something that is once defined – there are always new ones appearing, something that hasn’t been used before, or hasn’t been used in the same way. Security is not something set once, it is a process.
2.1. Social engineering
What if we know that house owner likes to go to a certain beach to swim – could we use that to try and steal the house keys from the shore, while he’s swimming? Or somehow get him to give us the keys, for a short while (as long as it takes to make a copy) – by presenting ourselves as handymen? This vector of attack is called social engineering. It is often used, yet it is often not taken into consideration.
This includes clicking on a link in an email where the sender (falsely) presents themselves as your bank, or YouTube, Google, your hosting provider, domain registrar etc. Always check headers when you are asked to click on a link, or give any data/information. Article on that: how to safely handle emails.
Same goes for giving access to your computer, smartphone, working area etc.
3. Weakest link – security as a chain
I touched on this in the previous chapter when discussing the vectors of attack. Security can be looked at in two ways. The first one is like a chain: as strong as its weakest link. The second one is explained in the next chapter.

Picture 2
Since I love analogies, here’s another suitable image:

Picture 3
How do you like the security in picture 3? Website related analogies would be:
- Excellent password, but insecure email account used for the password reset (account registration).
- Great password used in several different places (websites, accounts) – if either of them is hacked (password retrieved), the others are compromised as well.
- Good brute force protection (blocking a visitor’s IP address after X unsuccessful login attempts), but poor password (like: “admin123”).
- Not using encryption, or good security, relying solely on hiding the login link (a bad example of security through obscurity), often referred to by users as: “better than nothing” protection. Note though that security through obscurity is not bad in and of itself, it is bad only when it is the only security (or when it causes other problems).
I hope this is well explained. Now let’s make another take at security in general:
4. Layers – security as an onion
In this article, so far we have considered security only within one layer. Now, imagine the house from picture 1 and a fence with a gate, going all around it (not just blocking the entrance road as shown in picture 3). That would be an additional security layer. In picture 4, we’ll use an example that is relevant for websites:
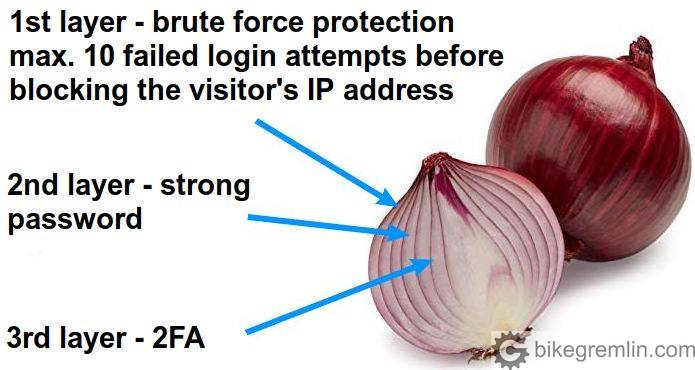
Picture 4
So, we have a 3 layer website login protection: 1st layer that will prevent guessing the password, by limiting the number of failed login attempts, 2nd layer that is a strong password (preferably with a username that isn’t publicly available, so that would have to be guessed as well), and 3rd layer that “saves the day” even if the first two layers are breached, i.e. if someone manages to “crack” the password.
We mustn’t forget prevention of physical access to the server by unauthorized persons – that is why it is important to choose reliable hosting providers.
5. Domain and website security – the big picture
- When you register a domain, you must first create an account with a domain registrar – providing an email address.
- For an account with a hosting provider, you must also provide an email address.
- WordPress websites, as you can probably guess, also require an email address for the administrator’s account.
You see where this is going? Why it is important to have a reliable email account?
Of course, this is all done from a computer (OK, many use smartphones, though I’m not sure how smart that is). I wrote about how to secure your computer, passwords, general safe habits etc. in the post about securing a (WordPress) website. I suggest you now read the first 5 chapters of that post, then come back here.
Now let’s take a look at what this story looks like shown in a graph:
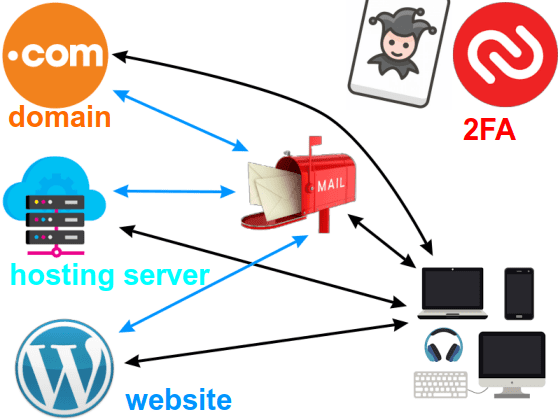
Picture 5
2FA is presented as a joker: it can be used to add protection to an email account, domain registrar, server, and website.
All the website contents can be restored from a website backup. A server brought down can be restored, or the website migrated to another server. However, if you lose your domain – it is very difficult to get it back (prove your ownership, and force the new “owner’s” domain registrar to transfer it back, or have your account reinstated to your control). Without gaining control of the domain back, all the previously acquired Google ranking, backlinks etc. will be lost (“…like the tears in the rain…”).
Likewise, if you loose control of the email account used for creating accounts with domain registrars (and other services), it is rather complicated to fix it (though not impossible).
To not forget the most important: use reliable domain registrars. I use and recommend Namecheap and Porkbun (affiliate links). You can read my reviews of Namecheap, and of Porkbun domain registrars.
6. How to protect yourself if hiring a developer / freelancer
For start: use reasonable caution and common sense, explained in detail in the 1st chapter.
Update 2024:
Regarding web hosting, agency, freelancer hiring etc, you might also want to read my article “Ask for better, not for cheaper.”
Next: website backup. If you have a lot of content, keep your own backup copy before hiring a 3rd party to work on the website.
Hosting account: if a third party needs to be given access to your hosting account (and FTP login isn’t sufficient), technically they could alter your password, while with many hosting providers, even contact info could be altered. Practically locking you out of your hosting account. If you are paying with PayPal, you’ll be able to stop any payments for additional services. If you have registered with a credit card (Visa etc.), then you might try disputing the charge over your bank. Either way, in case your login password gets changed, check with the developer what’s going on and if it still sounds suspicious, contact the hosting provider as soon as possible and have your account blocked – password and contact email reset to those under your control. Similar goes for any unexpected “purchases” through your hosting account (buying extra services etc.).
Reseller hosting account is very good for this, since the created sub-accounts can’t do any purchases, while their passwords and contact info can easily be changed / reset from your main reseller account.
DNS: If using Cloudflare, you could add another user, without giving them the ownership. Options are found in the “Members” section of the main menu. It would be wise to export DNS settings prior to that – just in case. Don’t know the situation with other DNS services when it comes to this.
If DNS is configured from the hosting account, then see under the “Hosting account” above.
Google Analytics: under “Admin” option within the main menu, under “Account User Management”, any Gmail account can be added, with set access rights (and they can be revoked when wanted). How to connect Google Analytics with a (WordPress) website.
Google Search Console: log in, click on “Settings”, then “Users and permissions”, and “Add user”. User rights can be “Full”, or “Restricted”. Google’s documentation explains the access details for both, under “Permission details”, on this link: Managing owners, users, and permissions. Post explaining how to connect a website to Google Search Console.
Domain registrar: if you trust someone enough to give them the keys to your home, then you could give them login for your domain registrar. I suppose. A developer could ask you to set certain nameservers with your registrar. Which is fine. Log in and configure nameservers yourself. Someone else logging into your domain registrar asks for a lot of trust and a rather good explanation why.
7. My personal opinion and experience
More access rights and more trust carries more responsibility. Most clients find me through recommendations. With most, I have a good relationship and a lot of trust. I’ve often had the opportunity to log in to hosting accounts, domain registrars, even order services using clients’ credit cards (all after being asked to). Many people simply find it more convenient to find someone they trust and not worry about the technical stuff.
Now, such a level of trust is surely flattering, but it is also a burden. I usually suggest that, even if I get the login passwords, they be changed after the job is done. In case of any problems: it is easier to find the culprit when the number of suspects is as small as possible.
Yes, exceptions can be made, for the people one has a long-lasting relation with, being practically a part of a team. Still, caution is not the same as doubt. I keep all the passwords in an encrypted format, for work I use a Linux computer with the encrypted disk and, because of my work, I’m more cautious than “normal people”. Are all the developers like that? I’d say: “I hope they aren’t”. 🙂
I don’t want this to sound like personal bragging, nor complaining about the clients. The main purpose of this post is to give some basic information about the security. To help people protect their domains and website contents – and all the hard work and money put into it.


Thanks for providing clear, concise and valuable info. This blog is amazing. SSL certificate is the best way to protect website. Sites with SSL testaments are given high priority by Google in SERP.