In this post I’ll explain how to avoid getting a virus, losing you computer data, or money from your bank account due to incautious email opening. I already wrote about safe habits when using a computer, but I think emails deserve some more explanation.
Contents:
- Introduction, or: this could really happen to you
1.1. Local company server security breach
1.2. Probable security breach cause analysis - Secure email handling
2.1. Common sense facts checking (logical check)
2.2. Technical checking of the received email validity
2.3. What if an email passes the logical, but doesn’t pass the technical check? - Conclusion and my personal opinion
1. Introduction, or: this could really happen to you
Introduction will be a bit long-winded (for a good reason), though you could skip to the 2nd chapter. The point is that many people know what and how to do to stay safe, but disregard it thinking it won’t happen to them. In my decades long IT experience: it happens to people every day. Omissions in computer security, email handling, or regular backup creation, are bound to bite you, sooner, or later. I don’t think a week goes by without me hearing: “Nooo, but how will I get my data back, it’s important?!”
1.1. Local company server security breach
What got me to writing this post was a situation with a local company that keeps track of all the payments for housing bills, Informatika. They store citizen data, along with all the houses and flats information, track paid and unpaid bills etc. After having logged in to check on my bills, this is what I got:
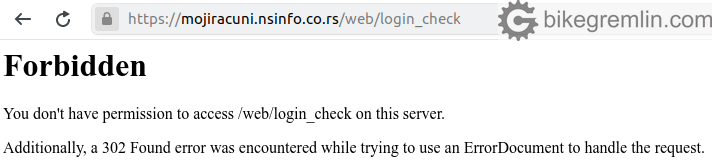
Picture 1
1.2. Probable security breach cause analysis
Since I don’t read the news (and don’t have a TV), I first Googled to figure out what has happened, after confirming that the problem is not on my (connection) end (how to determine website connection problem cause). Then I came to this post on a local news-portal (in Serbian). After reading the article I realized that the problem hasn’t been resolved for at least 24 hours (around 48 at the moment of writing this). Note this is a major local data processing company.
Disclaimer: to avoid any misunderstanding, of course I have nothing to do with the (most probably) criminal act, nor with the ongoing investigation, all the info given here is “as far as I can tell”, based on the publicly available information (no insider information whatsoever).
I will now offer the original news article (using my own translation from Serbian to English), with added translation to “honest, simple English”, based on my knowledge and experience, all for purely educational purposes, leaving the original text in italic:
- “There has been a hacker attack, most probably from abroad” – meaning: “We have no idea, who, why and how has hacked us.”
- “Based on our unofficial sources, the hacker attack was reported to the police tech. crimes division” – “This should put people at ease, so they believe the police will solve this, since we can’t, while we also wish to cover our backs”.
- “It is a new form of ‘ransomware’ virus that attacks antivirus protection and ‘backup’ systems, locking the files and making them inaccessible” – “We have no proper firewall and antivirus protection, nor secure off-site backups”.
- “Citizens shouldn’t fear any private data abuse from this hacker attack, because database is stored on a separate platform” – “If you take the above shown statements into account, along with the fact that we couldn’t get it back up and running for days now, you needn’t worry – because it won’t do you any good”.
How can an attack like this happen? There are thousands of ways, with new ones being invented all the time. 100% secure system is an unusable system, by definition. In other words, every website, server, or a database will be hacked sooner, or later. The point is to have reliable, tested backups, and to store any sensitive information in an encrypted form (no mention of that in the “official report”), so they are unusable to any hacker.
Yet, the above noted doesn’t mean that one shouldn’t do what’s up to them to make hackers’ job more difficult and increase security. One of those things, and, in my opinion, a probable cause of this hack, is secure email handling, which is the main topic of this post.
2. Secure email handling
Often used hacking method is sending spoofed emails. What does it look like? For educational purposes, I have sent a spoofed email to my Gmail address, presenting myself as “Your Bank”. Here’s what it looks like:
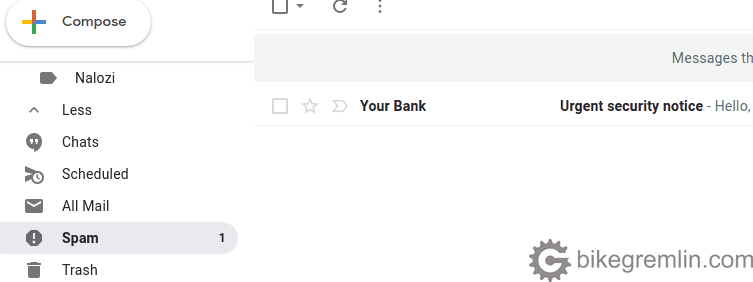
Picture 2
For start, Gmail client had correctly recognized the email as falsified, placing it in the “Spam” folder. That is a first sign for caution.
By the way, Gmail client has an excellent spam filter, plus it scans all the received and sent emails for viruses. How to connect your (domain) email with Gmail client.
Still, it happens that email clients recognize even legitimate emails as spam, that is called “false positive“. So we’ll give our falsified email the benefit of the doubt and double check (do not click on any links inside the email, until you check everything!).
2.1. Common sense facts checking (logical check)
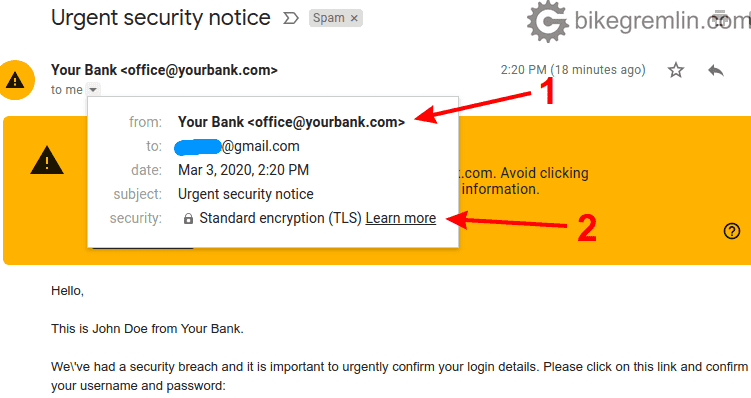
Check the (alleged) sender address (1) and see if encryption was used (2)
Picture 3
If your bank has their website on “yourbank.com” domain, then this looks OK for now (read on). Go to your bank’s website and double check. If the website is on “yourbank.us”, then by all means check with someone at the bank if they have started using .com domain. If not, then the email is most probably spoofed.
When it comes to this, hackers can be very creative. Using “yourbank.co.uk” (instead of your bank’s “yourbank.uk”, or “yourbank.com” for example).
Another often used trick is “yourbank.client-contact.com”, which is in fact a “yourbank” subdomain of the “client-contact.com” domain, and has nothing to do with “yourbank.com”. For example, domain “bank-client-contact.com” is free now, I could register it right away, then create a subdomain “yourbank.bank-client-contact.com”. Email sent from say “[email protected]” would pass all the checks (SPF, DKIM, IP), except for this simple, common sense, facts check. More detailed explanation domains is here: what is a domain, and a subdomain. Shortly put: domain is only the last part, before the extension (.com, .uk etc.). Anything at the start, divided by a dot is a subdomain (such as io.bikegremlin.com, which is a subdomain of bikegremlin.com domain).
Other important checks that have nothing to do with any technical aspects, but boil down to simple reasoning are the following:
- Is your name written correctly in the recipient field, or within the email text?
- Does the emails design (visual look) resemble other emails from the sender?
- Even if the email has some “urgency”, take a deep breath, re-read it and see if anything looks suspicious.
- Check the sender’s domain, as explained above.
- If an email comes from a friend, or a business partner, but the contents look odd, double check using other means (phone etc.), since it could be that their computer, or/and email account were hacked.
- Not strictly related to emails, but the same goes for anyone pretending to be your friend, creating a new Facebook account with your friend’s profile picture. Sending you a link to click, or asking for help, urgently. Do double check before clicking on anything. This also goes for any hacked real accounts of your friends on any social network. If a message is in any way odd, especially if you are asked to click on a link, be cautious and check.
These types of attack are called social engineering.
If any of these don’t check out, it’s safer to mark the email as spam and delete it, without clicking on any links in it. Here’s another example of an email that Gmail finds to be suspicious, this one is marked more discretely:
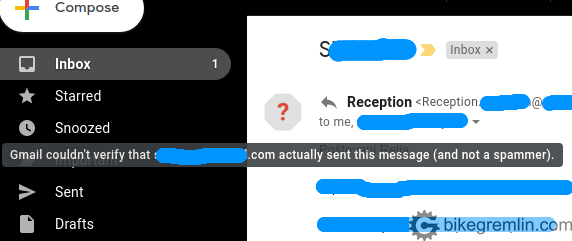
Picture 4
Here too is the same checking procedure as explained above. Only if an email checks out with this “logical check”, should you look for the technical aspects, as explained in the next chapter. However, don’t rely only on one check method, they should both check out, before an email is considered legit, not spoofed.
2.2. Technical checking of the received email validity
Only if the email checks out the above explained common sense check, should you continue and check the technical aspect (otherwise, it could be a well falsified email that passes the technical checkup). This technical check sounds more complicated than it is, it’s fairly simple. It requires checking the email header. Here’s how it’s done with Gmail:
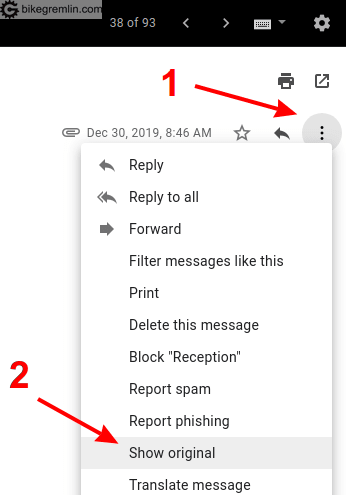
Click on the three dots (1), then on “Show original” (2)
Picture 5
After that, Gmail shows the email’s header, but first, on top, it shows the results of its own analysis, which is very convenient:
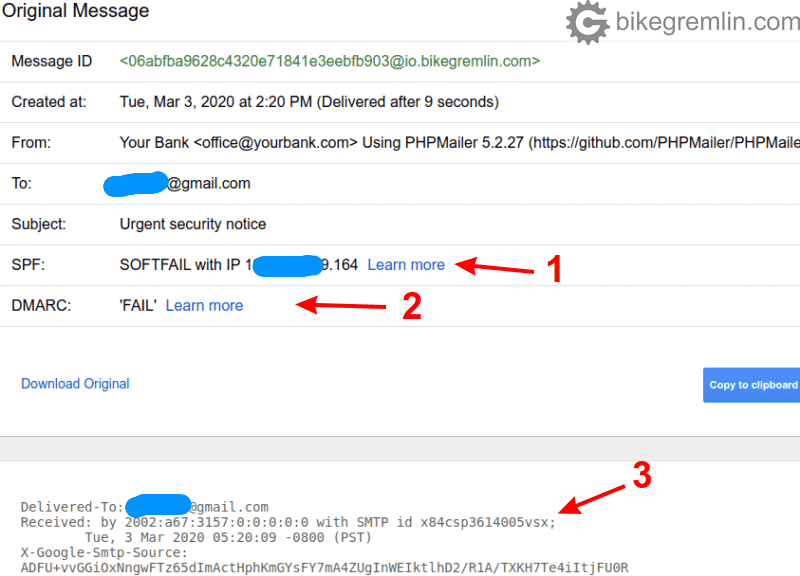
See if there are any “SPF” (1), DMARC (2), or DKIM validation errors
Or copy the header (3) to an email header analyzer tool
Picture 6
Another example of an email that doesn’t check out:
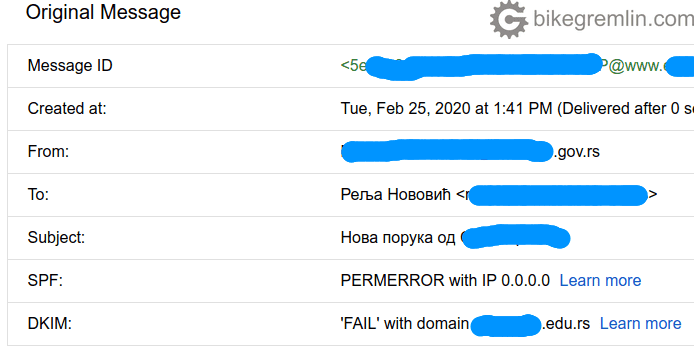
Picture 7
With Gmail it’s practical that it does all the checks and notifies you right away (shown in pictures 3, 4, 6, and 7). Still, all the email clients have an option of checking email’s header. You can always copy-paste it to an email header analysis tool (link to a Google’s tool). The options are usually called “show header”, “view source”, or “show MIME header” (“Multipurpose Internet Mail Extensions”), depending on the particular email client used.
Here’s what Google’s email header analysis tool looks like:
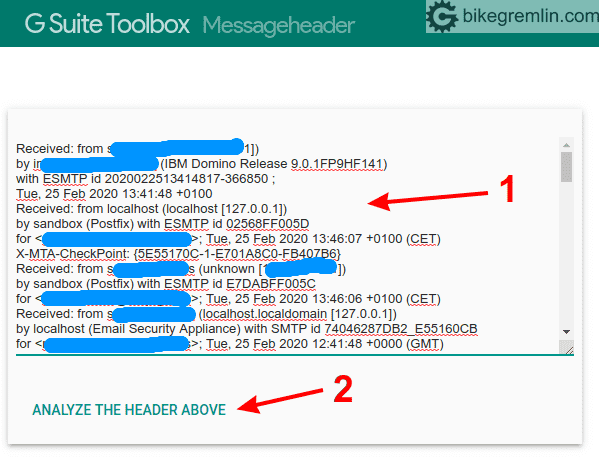
Just paste the header info (1) and click “Analyze the header above” (2)
Picture 8
Nakon toga, dobićete izveštaj provere:
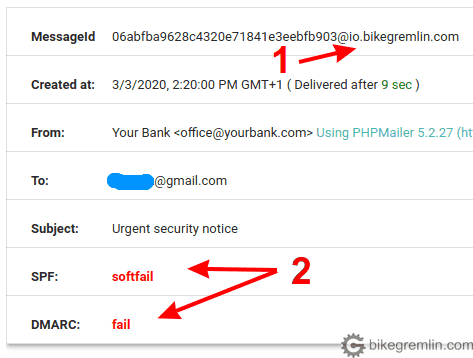
I didn’t even hide the sending domain properly (1), while SPF and DMARC validation fails are also shown (2)
Picture 9
For an example, here as an email that is legit, properly configured, and passes all the logical and technical checks:
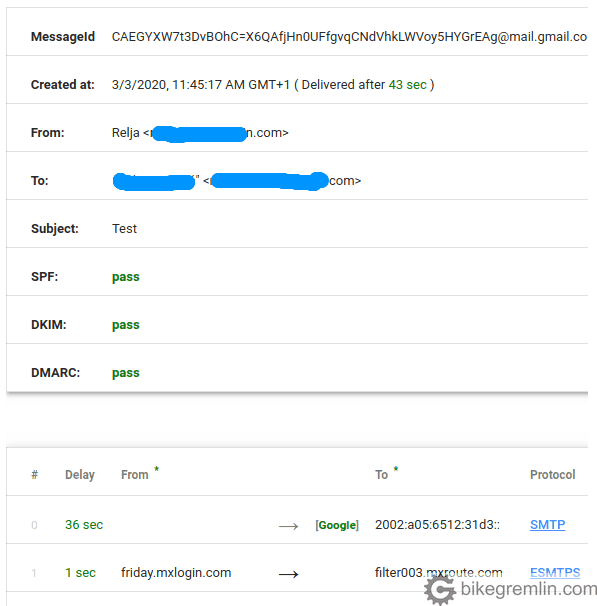
Picture 10
Another tool worth checking a suspicious email’s header with is MXtoolbox email header analyzer. This is what a legit and well technically configured email looks like:
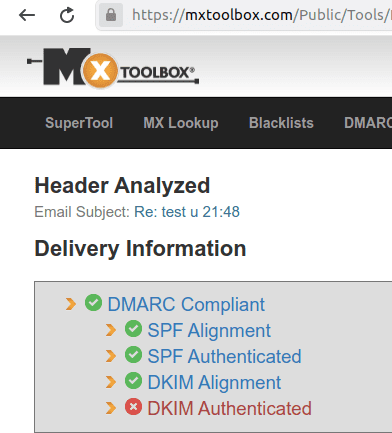
Picture 11
Don’t let the red “DKIM Authenticated” worry you, that is often the case when using Gmail as a mail client. What matters is that DMARC, SPF and DKIM (all the other fields checked) are OK.
This is what poorly configured email looks like, one that can easily be spoofed (in this particular case it wasn’t, but Serbian e-government hadn’t configured their email properly, so it can be more easily spoofed and abused, but that’s not the topic of this post):
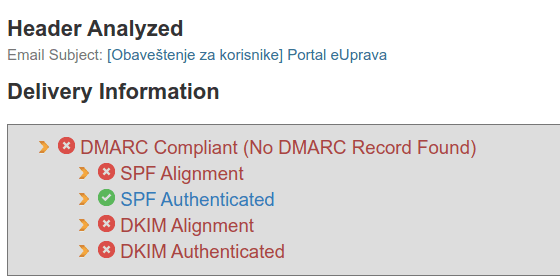
2.3. What if an email passes the logical, but doesn’t pass the technical check?
I wrote about how to configure domain email, including the DMARC policy for blocking any invalid emails. If your domain’s email is configured as explained in that post, with properly configured DMARC TXT DNS record, no one should be able to send emails that appear to be coming from your domain. Such emails will be blocked by most mail servers.
Unfortunately, in my experience, many people, including some large companies, or government services, including some security services, disregard these security settings. I even experienced a scenario similar to this one:
- Companies A and B do business with each other.
- Company A doesn’t have properly configured email related records in their DNS.
- Spam filter of company B, justifiably blocks emails sent from company A, because those emails don’t pass validation (for the above mentioned reason).
- I get consulted about the problems (and, during analysis, I figure out the above noted facts).
- I point out the problem and explain how DNS records should be configured. I also explain that wrongly configured DMARC record makes it easier for anyone to send emails, falsely presenting themselves as the company A.
- Company A looks for second opinions and hears that the problem can be mitigated by company B “telling” their spam filter to accept all emails send from the company A, even if they don’t pass the validation (this is called “whitelisting” – placing an email address, or a sending domain in the whitelist).
- Companies A and B agree to implement the “whitelisting” solution, because “it’s easier, that other stuff is too difficult, too complicated, we tried”?!?
- Company B will now, when they get an email claiming to be coming from company A, let that email to their inbox and, most probably, treat it as a legit email. Managers are happy and the business is good. Occasionally, someone might open and click on a link in a spoofed email, compromise some data, perhaps get a virus… Who knows?
Now, imagine companies, like the ones in the story above, who deal with sensitive customer data. As they say: space and human stupidity are endless, though I’m not 100% sure about the space.
So think twice if doing business with a company who’s emails don’t pass the technical check – do you want to give them any data.
3. Conclusion and my personal opinion
There are a lot of frauds and lots of abuse. This makes it hard to stay safe on the Internet. However, one should at least try, make a sensible effort to be educated and safe, not be an easy pray to swindlers.
Make regular backups. Keep all the important data, especially that of other people, in an encrypted form, so they can’t easily be taken and exploited.
Finally, you don’t have to be a “computer genius” to be safe on-line, it is enough to use common sense and reasonable caution, as you would use in “the real world” and live communication.

